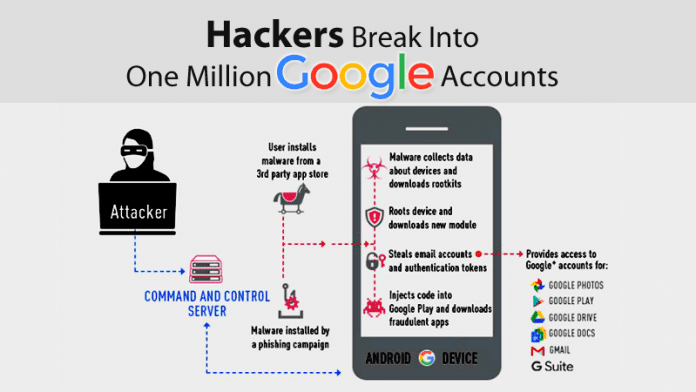
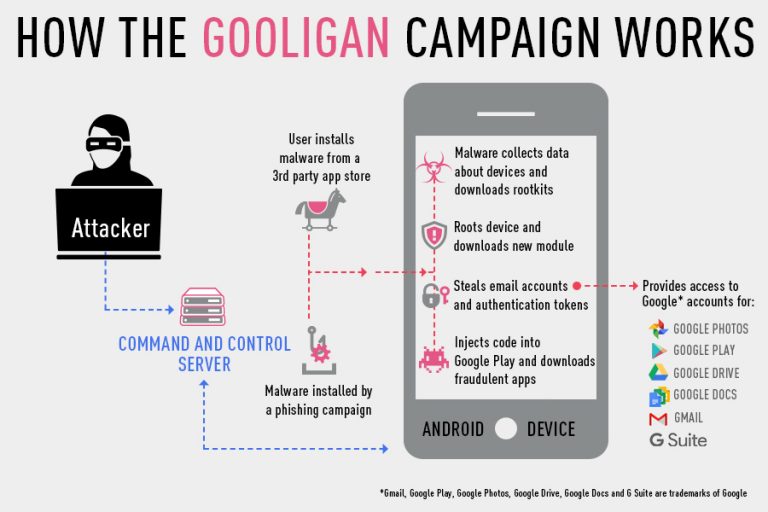
The security company Check Point has announced that its security researchers discovered a new malware variant for Android that attacked more than one million Google accounts. The new malware campaign, dubbed as “Gooligan” is rooting for Android devices and steal email addresses and authentication credentials. With this information, attackers can access sensitive data stored on users Gmail, Google Photos, Google Docs, Google Play, Google Drive and G Suite. “This data theft of more than one million Google accounts is extremely alarming and represents a new era of cybercrime. We are seeing a change in the strategy of hackers who now have more and more as the preferred target mobile devices, in order to steal sensitive information in them are stored”. Says Michael Shaulov, responsible for mobile security solutions from Check Point. In round numbers, this campaign is affecting 13,000 devices per day and is the first to be able to attack more than one million devices. Alongside this, there are hundreds of email addresses that are associated with business accounts worldwide. What increases exponentially contagion. The Gooligan has targeted devices with Android 4.0, 4.3, 4.4 (Icecream sandwich, Jelly Bean, KitKat) and 5.0 (Lollipop), accounting for nearly 74% of all Android devices in use. After the attackers manage to get a grip on the device, simply it generates revenue through the fraudulent installation of Google Play apps, classifying them in the name of the victim. Every day, the Gooligan installs at least 30,000 apps on compromised devices, which means more than two million apps since the start of this campaign. The company once detected this new threat, contacted Google security team to inform them about the campaign. Google responded immediately, stating that this cooperation between the two companies allows a fierce and faster action defending users from malware family Ghost Push. The American company relates, the voice of Adrian Ludwig, Android security officer of Google, which has taken many measures to protect its users and improve the security of Android ecosystem as a whole. Among other measures, Google contacted all affected users and revoked their credentials for access, even removing the apps associated with Ghost Push family from their official Google Play store and adding new protections to its Apps with Verify technology. Gooligan was detected in the malicious app SnapPea. Check Point Research Team dedicated to mobile devices, first found traces of Gooligan code in the malicious app SnapPea last year. In August 2016, the malware reappeared with this new variant and has since infected at least 13,000 devices per day. About 57% of these devices are located in Asia and about 9% in Europe. Hundreds of exposed emails are associated with companies around the world. The infection begins when the user downloads and installs an infected app with Gooligan which simply makes the Android device vulnerable or via clicks on a malicious link in a phishing message (which comes mostly by email). After that simply the criminals can access tokens that are important for the accreditation of users to Google ecosystem. Make sure you are infected or not? The security firm, Check Point is offering a free online tool that allows users to check their Google accounts were affected or not, click here simply to scan or analyze your Google account. However, Michael Shaulov says that “If your account has been attacked, it is advisable that you must reinstall the operating system of your device. This complex process is called flashing and therefore we recommend that you first disconnect the device and take it to a certified technician to carry out this operation”.
Here is the list of fake apps infected by Gooligan:-
Perfect Cleaner # Demo # WiFi Enhancer # Snake # gla.pev.zvh # Html5 Games # Demm # memory booster # แข่งรถสุดโหด # StopWatch # Clear # ballSmove_004 # Flashlight Free # memory booste # Touch Beauty # Demoad # Small Blue Point # Battery Monitor # 清理大师 # UC Mini # Shadow Crush # Sex Photo # 小白点 # tub.ajy.ics # Hip Good # Memory Booster # phone booster # SettingService # Wifi Master # Fruit Slots # System Booster # Dircet Browser # FUNNY DROPS # Puzzle Bubble-Pet Paradise # GPS # Light Browser # Clean Master # YouTube Downloader # KXService # Best Wallpapers # Smart Touch # Light Advanced # SmartFolder # youtubeplayer # Beautiful Alarm # PronClub # Detecting instrument # Calculator # GPS Speed # Fast Cleaner # Blue Point # CakeSweety # Pedometer # Compass Lite # Fingerprint unlock # PornClub # com.browser.provider # Assistive Touch # Sex Cademy # OneKeyLock # Wifi Speed Pro # Minibooster # com.so.itouch # com.fabullacop.loudcallernameringtone # Kiss Browser # Weather # Chrono Marker # Slots Mania # Multifunction Flashlight # So Hot # Google # HotH5Games # Swamm Browser # Billiards # TcashDemo # Sexy hot wallpaper # Wifi Accelerate # Simple Calculator # Daily Racing # Talking Tom 3 # com.example.ddeo # Test # Hot Photo # QPlay # Virtual # Music Cloud